Zero-Click Location Leak: The Privacy Flaw Hiding in Your Messaging Apps


In an era where digital privacy is increasingly precious, a recently discovered vulnerability in popular communication platforms like Discord and Signal has raised serious concerns about user location privacy. This vulnerability, which requires nothing more than sending a friend request or an emoji reaction, can reveal a user's approximate geographical location - all without any interaction from the target user.
The Discovery
The vulnerability was uncovered by security researcher "Hackermon", who detailed a zero-click deanonymization attack that affects not just Discord and Signal, but potentially hundreds of other platforms. What makes this discovery particularly concerning is its simplicity and stealth - victims have no way of knowing they're being targeted, and the attack can be executed through seemingly innocent actions like friend requests.
Understanding the Technical Foundation
To grasp how this vulnerability works, we need to understand a fundamental aspect of modern internet infrastructure: Content Delivery Networks (CDNs). Companies like Cloudflare operate these networks to make the internet faster and more efficient.
How CDNs Work
Imagine you're in Seattle trying to view an image stored on a server in London. Without a CDN, your request would need to travel across the Atlantic Ocean and back - not ideal for instant messaging! CDNs solve this by maintaining a network of servers worldwide that keep copies (caches) of frequently accessed content. When you request that image, you'll receive it from the nearest server rather than from London.
This is where Cloudflare's system comes into play. When you receive a Discord notification with an avatar image, that image gets cached on the Cloudflare server nearest to you. This caching system is designed for performance, but as we're about to see, it can inadvertently reveal more than intended.
The Mechanics of the Exploit
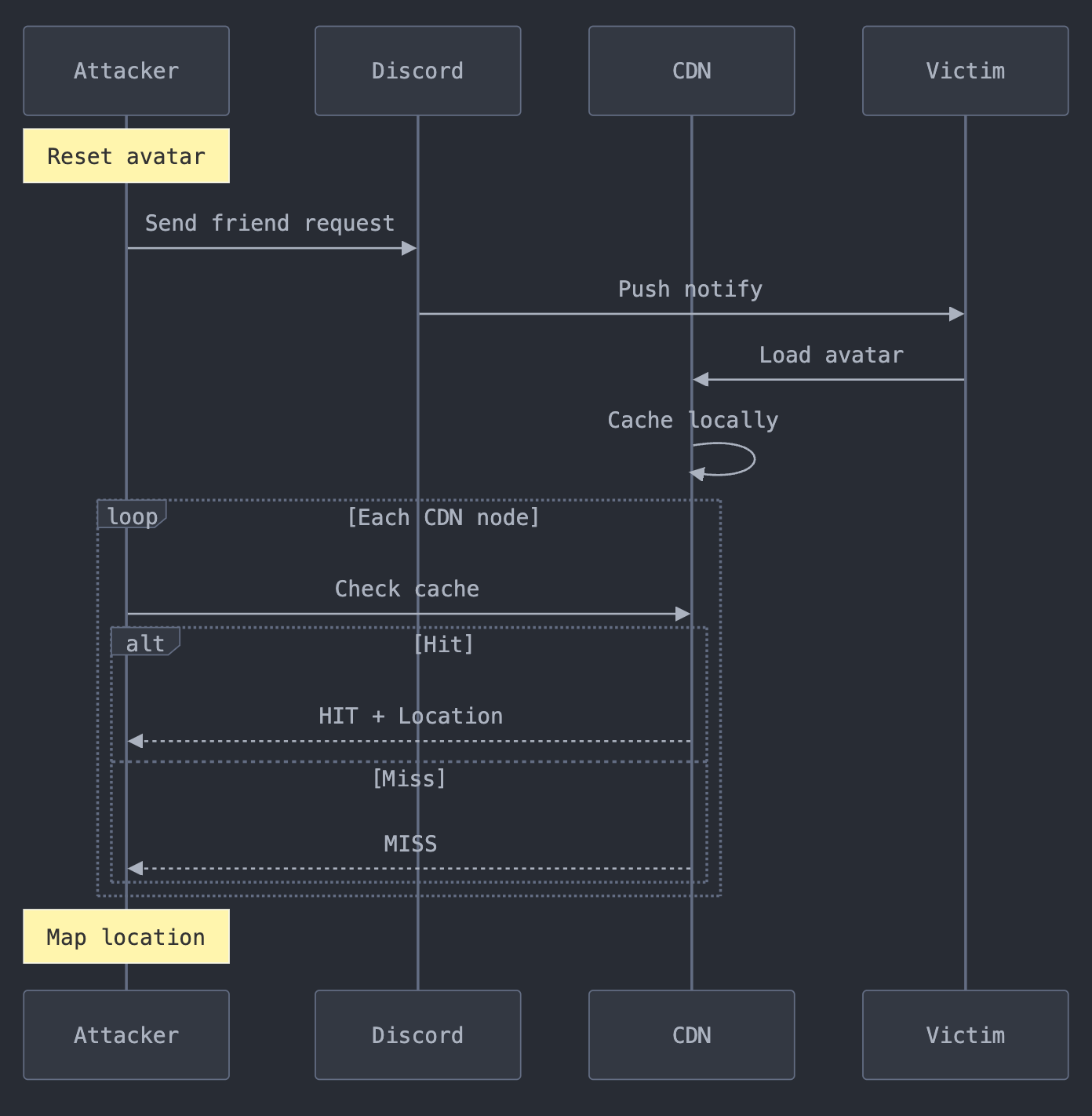
The vulnerability leverages two key aspects of how Discord and Cloudflare interact:
- Automatic Content Loading: When you receive a Discord friend request, your device automatically loads the requester's avatar image - even if you never open Discord.
- CDN Caching Behavior: The image gets cached at the Cloudflare server closest to your location, leaving a digital fingerprint that can be traced.
What makes this particularly clever is how it takes advantage of Discord's different URL formats for the same avatar image:
- Push notification format: Ends with an avatar hash
- Website display format: Ends with "avatar.png"
These different URLs for the same image are cached separately, allowing an attacker to specifically track which notification-format URLs have been cached - and therefore, where the target user might be located.
The Friend Request Attack Vector
Real-World Validation
During testing, researchers successfully demonstrated this attack against multiple targets, including Discord's CTO. The attack provided location accuracy varying from city-level precision in urban areas to broader regional identification in less populated zones.
Technical Implementation
The friend request method represents the most straightforward and reliable attack vector, requiring no user interaction to execute successfully. The attack leverages Discord's automatic avatar loading system in push notifications.
Step 1: Avatar Setup
- Upload fresh image to reset cache state
- Ensure unique image hash generation
- Verify successful avatar update
Step 2: URL Format Analysis
Discord generates two distinct URLs for the same avatar:
# Example
# Push Notification Format
cdn.discordapp.com/avatars/123456789/[hash]
# Website Display Format
cdn.discordapp.com/avatars/123456789/[hash].png
These URLs, while pointing to identical content, maintain separate cache entries in Cloudflare's CDN.
Step 3: Attack Execution
- Send friend request to target
- Discord pushes notification with avatar
- Target device automatically loads avatar
- CDN caches image at nearest datacenter
Step 4: Location Discovery
Monitor CDN servers for cache hits:
Response Headers:
CF-Cache-Status: HIT
CF-Ray: 6b5d4c32-LAX # LAX indicates Los Angeles datacenterThe attack's effectiveness stems from its invisibility - targets see only a standard friend request notification, with no indication that their location is being leaked through CDN behavior analysis.
Key Technical Aspects
- Zero-click execution
- No user interaction needed
- Works with Discord closed
- Bypasses standard privacy controls
- Leaves no suspicious traces
Implementation Notes
The attack succeeds because Discord's push notification system:
- Automatically loads avatars
- Uses predictable URL patterns
- Relies on geographically distributed CDN
- Maintains separate cache entries
- Exposes CDN metadata in headers
The Emoji Reaction Alternative

Overview
While the friend request method offers a straightforward approach, the emoji reaction attack vector provides a more sophisticated alternative that bypasses standard privacy controls. This method exploits Discord's emoji rendering system to reveal user locations, even when friend requests are disabled.
Why It's Concerning
The emoji attack is particularly effective because:
- It bypasses friend request privacy settings
- Works in any shared Discord server
- Appears as normal chat behavior
- Cannot be easily disabled without limiting core Discord functionality
Technical Implementation
Emoji URL Variations
Discord generates multiple URL formats for each emoji:
cdn.discordapp.com/emojis/{id}.png
cdn.discordapp.com/emojis/{id}.gif
cdn.discordapp.com/emojis/{id}.webp
cdn.discordapp.com/emojis/{id}?size=48
// Plus various size and format combinations
This results in 124 distinct URLs per emoji that must be checked. However, understanding Discord's asset delivery patterns can reduce this to 62 high-probability URLs.
Attack Execution Process
- Initial Setup
- Block Discord CDN on attacker's device
- Prepare network request monitoring
- Select target emoji
- URL Generation
- Create URL list for all format variations
- Generate size parameter combinations
- Map potential CDN endpoints
Cache Detection
For each Cloudflare datacenter:
GET /emojis/{id}.{format} HTTP/1.1
Host: cdn.discordapp.com
Look for response headers:
CF-Cache-Status: HIT/MISS
CF-Ray: xxxxx-LAX
The hacker will also need to prevent Self-Interference
The key technical challenge is preventing the attacker's own device from contaminating the results:
Network Controls
- Block outbound CDN requests
- Monitor HTTP response headers
- Filter cached content markers
Cache Isolation
- Use separate browsing contexts
- Clear CDN caches between tests
- Validate cache status responses
Foundation: CDN Behavior
The attack leverages two critical Cloudflare CDN headers:
CF-Cache-Status: HIT # Indicates cached content
CF-Ray: 6b5d4c32-LAX # Shows datacenter location
These headers reveal both cache status and server location, enabling geographical tracking through CDN behavior analysis.
Understanding the Accuracy and Limitations
Like most technical exploits, this one comes with both strengths and limitations that affect its real-world impact.
Geographic Precision
The accuracy of location identification varies significantly:
- In urban areas with multiple Cloudflare data centers, the location might be narrowed down to a specific city
- In rural areas or regions with fewer data centers, the location estimate could span multiple states or regions
- Some results show multiple possible locations due to how CDN load balancing works
- Multiple devices can trigger different cache locations
- In the Cloudflare CDN example, if a victim was in Western Australia, it would show them either in Asia or somewhere in the east of Australia.
For example, when tested with a VPN in Phoenix, the system identified both Phoenix and Dallas as possible locations. This isn't necessarily a flaw - it could indicate multiple devices accessing Discord or the way Cloudflare balances load across its network.
Technical Limitations
Request Routing
- Can't directly query individual Cloudflare data centers
- Must rely on natural CDN behavior
- Requires indirect observation
Cache Interference
- Must prevent self-caching
- Need to handle multiple device scenarios
- Load balancing can complicate results
Server Distribution
- Accuracy depends on Cloudflare server network
- Some regions have sparse coverage
- Results can be ambiguous in certain areas
Implementation Challenges
Emoji Method Complexity
- Must handle multiple URL formats
- Requires network request blocking
- More complex execution but harder to prevent
Friend Request Method
- Simpler implementation
- More reliable results
- Can be blocked by privacy settings
General Considerations
- Need to handle load balancing scenarios
- Must account for multiple devices
- Required precise timing in some cases
The exploit demonstrates how optimization features (CDN caching) can inadvertently create privacy vulnerabilities. The technical implementation, while not highly complex, shows clever use of understanding how content delivery networks operate and how their normal behavior can be leveraged to reveal information not intended to be exposed.
Privacy Implications and Real-World Impact
The significance of this vulnerability varies dramatically depending on who you are and how you use Discord or Signal.
For Average Users
For most Discord users who primarily use the platform to chat with friends and gaming communities, this vulnerability might seem more interesting than threatening. After all, knowing someone is "somewhere in New York City" (population 8.8 million) isn't particularly useful for malicious purposes.
However, there are scenarios where even this general location information could be problematic:
- Online harassment campaigns where attackers try to gather any available information about their targets
- Stalking situations where an attacker is trying to narrow down a victim's location
- Social engineering attacks that use location information to make scams more convincing
For High-Risk Users
The implications become more serious for certain categories of users:
Journalists and Activists
- May need to keep their location private for safety reasons
- Could be targeted by state actors or hostile organizations
- Might be using platforms like Signal specifically for their privacy features
Privacy-Conscious Individuals
- People who deliberately keep their location private
- Those who may be stalking or harassment targets
- Individuals whose work requires location privacy
Business Users
- Corporate executives whose location could reveal business activities
- Employees handling sensitive negotiations
- People whose movements might reveal confidential information
For these users, the ability to determine their approximate location through something as simple as a friend request or emoji reaction represents a significant security concern.
Mitigation Strategies
While this vulnerability raises serious privacy concerns, there are several ways users can protect themselves.
Immediate Steps for Users
Use a VPN
- A reliable VPN service will mask your true location
- Ensures that CDN caching occurs at the VPN server location instead of your actual location
- Provides protection against this and many other types of privacy leaks
Adjust Platform Settings
- Disable friend requests on Discord when you are not expecting one
- Consider disabling push notifications
- Be selective about which servers you join and who can interact with you
Practice Privacy-Conscious Behavior
- Be cautious about friend requests from unknown users
- Consider using alternative platforms for sensitive communications
- Regularly review and update privacy settings
Broader Implications for Online Privacy
This vulnerability highlights several important lessons about privacy in our connected world.
The Privacy-Performance Trade-off
The root of this vulnerability lies in a system designed to make services faster and more efficient. CDNs are a crucial part of modern internet infrastructure, enabling the quick loading times we've come to expect. However, this case demonstrates how optimization for performance can sometimes create unexpected privacy implications.
This trade-off between privacy and performance is not unique to CDNs. It's a fundamental challenge in modern technology:
- Push notifications provide convenience but can leak information
- Location services make apps more useful but track our movements
- Social features connect us but can expose personal information
The Future of Privacy Engineering
This vulnerability also raises important questions about how we design privacy-conscious systems:
Architectural Considerations
- How can we build systems that are both fast and private?
- What privacy implications should architects consider when designing distributed systems?
- How can we better balance user experience with privacy protection?
User Control
- What level of control should users have over privacy-impacting features?
- How can we make privacy settings more accessible and understandable?
- What's the right balance between security and usability?
Conclusion
The Discord and Signal CDN location leak vulnerability serves as a reminder that privacy threats often lurk in unexpected places. What seems like an innocent feature - a friend request notification or an emoji reaction - can potentially reveal more than intended about a user's location.
For most users, this vulnerability might not represent a serious threat, but its existence highlights the ongoing challenges of maintaining privacy in our connected world. It reminds us that convenience features often come with privacy trade-offs, and that maintaining digital privacy requires constant vigilance.
As we continue to build and use online platforms, we must remain mindful of these trade-offs and work to create systems that respect both user privacy and user experience. Until then, understanding these vulnerabilities and taking appropriate precautions remains our best defense against unwanted privacy breaches.
Key Takeaways
- Simple actions like friend requests can potentially reveal user locations
- Privacy vulnerabilities often arise from performance optimization features
- Different users face different levels of risk from such vulnerabilities
- Mitigation strategies exist but require active implementation
- Privacy engineering faces ongoing challenges in balancing competing needs
As technology continues to evolve, new privacy challenges will inevitably emerge. Staying informed and maintaining good privacy practices remains crucial for all internet users, regardless of their risk level or privacy concerns.
Here is hackermon's article: https://gist.github.com/hackermondev/...
And here is a well made video on the same topic by No Text To Speech
Primary Tag: [Network Security]
Technical Level: [Intermediate] [Technical]
Content Type: [Technical Deep Dive] [Security Analysis] [Vulnerability Report] Specific Technologies: [CDN] [Discord] [Signal] [Cloudflare] [Push Notifications] Problem-Solving: [Privacy Protection] [Location Security] [Data Leakage] [Attack Vectors]
Special Considerations: [Zero-Click Attacks] [Digital Privacy] [Real-World Impact] [Active Threats]


